If That Email Looks A Little Suspicious, It Probably Is!
One of the easiest ways to prevent cyber attacks is by understanding phishing and other suspicious emails.
Have you ever opened your inbox only to find an out-of-the-ordinary email requesting access to your account?
Maybe it was an email saying your account was expiring?
It could even have been an email from someone on your team (or at least the name sounds familiar) and they are asking you to review a document.
Hackers are more sophisticated than ever.
Additionally, every day they seem to become savvier in their approach to stealing your information.
Because even large-scale organizations like the UN can fall victim to hackers.
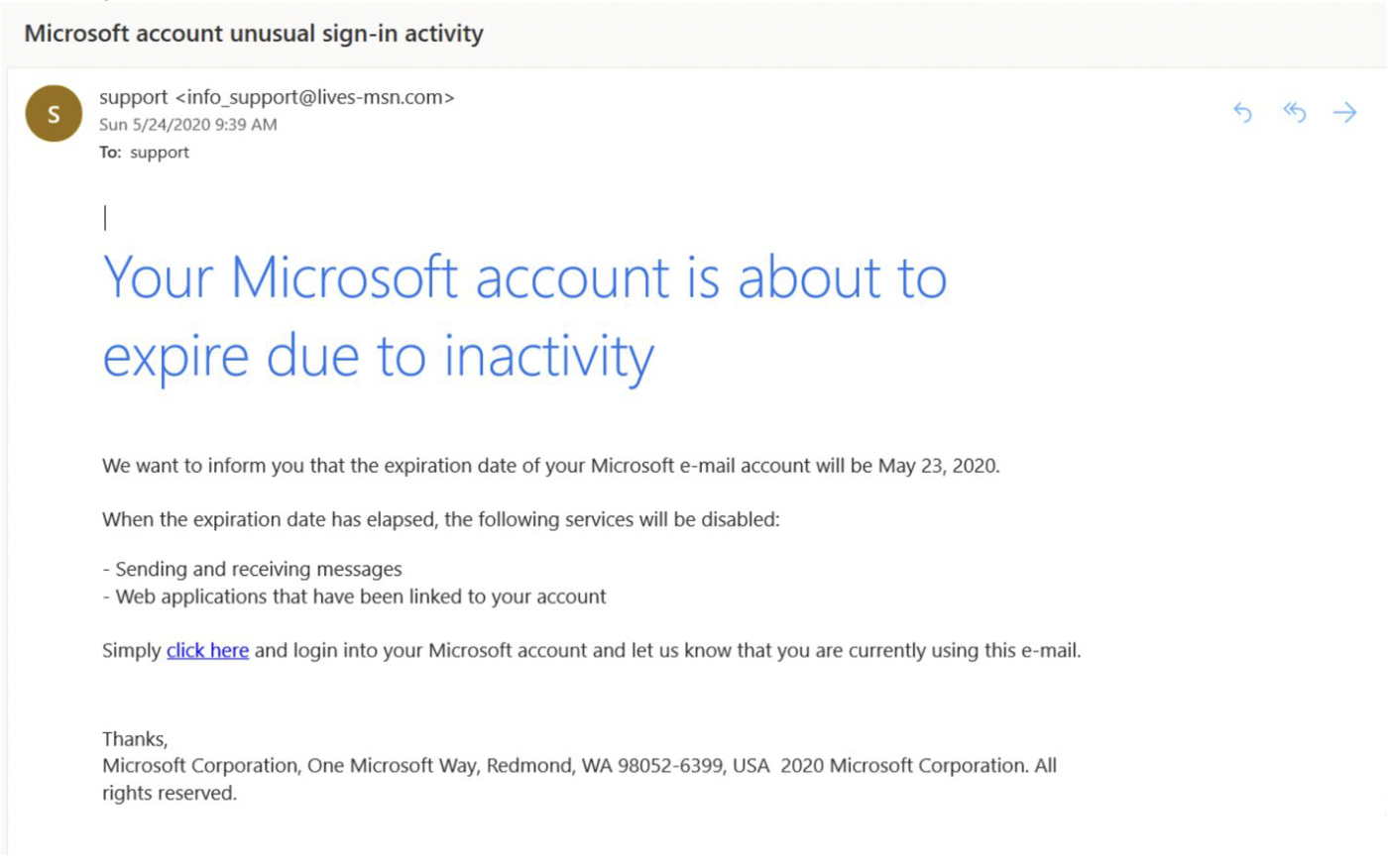
Take a look at this email:
Most users won’t see this email as a problem.
What’s The Problem?
This seems normal.
The copy in the email is consistent with Microsoft.
Also, the font at the top of the email is consistent with Microsoft’s standards.
Microsoft’s address is at the bottom. It even comes from a support email.
So, what’s the issue?
When you click on the link to “log in” to your Microsoft account, you’ve infected your computer and that is the issue.
Now, hackers have access to your payment information, addresses, and passwords.
They can even access your contact list and can email your friends, family, and business associates in an attempt to get their information.
Even worse, a clever email scammer can get into the settings of your emails and set rules that render your email unable to send out and receive any emails without warning, or auto deletes further suspicious emails so that you are not aware you have been hacked until it is far too late.
Simple oversights like this are ways to prevent cyber attacks.
Beyond individual user account vulnerabilities, every company should be aware of the risks to their IT networks, including their M365 and SharePoint environments.
Things such as suspicious log-ins are always an immediate red flag.
For example, why is someone able to access your SharePoint site if they had their access taken away?
Or how does someone have access to an account on your network from a location outside of where they live?
These are vulnerabilities for many businesses, but they don’t have to be. There are ways you can prevent cyber attacks.
And the best way to minimize the risk of a cyber-attack is through prevention.
SLAM Those Suspect Emails!
Creating security policies like password guidelines and then training employees is a good place to start.
A great tool when training employees is called the SLAM method. SLAM stands for:
- Sender
- Links
- Attachments
- Message
Before opening an email or clicking on an email link, check the SENDER to see if there is anything suspicious, like a misspelled or different domain.
Then, review but don’t open, the LINK(S) and/or any ATTACHMENTS.
Lastly, read the email subject line and MESSAGE noting anything unusual like strange characters or grammar.
If anything about the email is suspicious, do not open or click anything and notify the IT department if appropriate.
It’s Time to Plug the Leak in Your Passwords!
Another way to protect yourself and your company is by protecting your passwords.
Have you ever forgotten your password?
It happens to everyone, but there’s an easy solution.
All you do is simply reset your password with the password reset form.
In fact, resetting your password is so easy you have to wonder how easy it might be for someone else to do it.
Well as it turns out if someone has access to your credentials, it is that easy for them to
reset your password without you knowing.
In an instant, this simple action locks you out of every account that email and password are tied to.
To make matters worse, if the hacker is even a little bit clever, they can change certain settings inside of your personal profile making it impossible for you to quickly prove that you are “you” when recovering your own password.
The cherry on top is that often bundled in with this horrendous inconvenience the hacker will often use the opportunity to charge you exorbitant amounts of money to get your account back.
It’s bad enough if this issue has affected one employee in a company, but depending on the stability of your cyber security infrastructure, the problems that arise from your leaked credentials can cascade throughout your entire office affecting every single user account in your company.
This goes without saying that if this problem were to cascade to every single computer, it would put the business on hold and your company out of commission for weeks, if not months.
Trying to solve this problem would cost your company immensely more money than it would have cost to prevent the problem from happening in the first place.
Smart prevention actions for users could include a password manager or two-factor authentication.
But what about prevention options for your M365 or SharePoint network?
Bamboo Security Audit Plus Gives You Ways To Prevent Cyber Attacks:
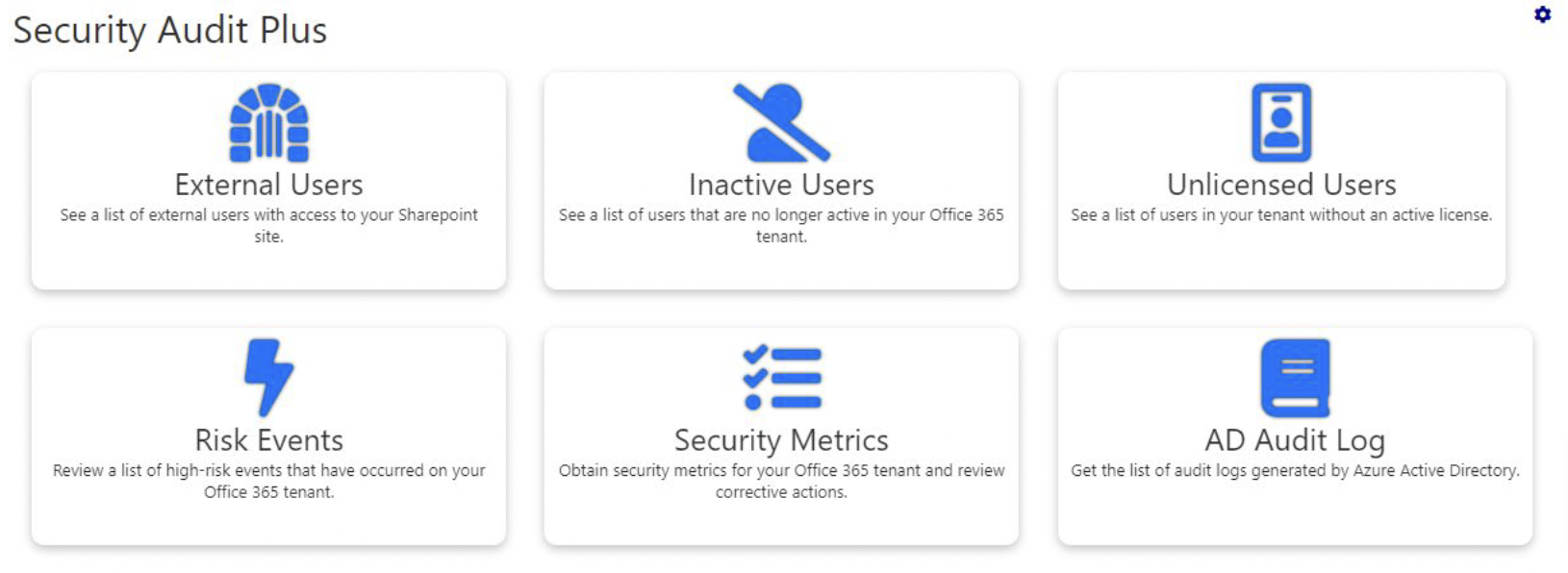
Our latest product offering, Security Audit Plus, enables you to quickly and easily audit your M365/SharePoint environment’s security risks.
Using our simple dashboard, you can review:
- Identity Protection
- User Reports
- Access/Permissions
- Security and Risk Protection
User Security Risk Management
Security Audit Plus offers multiple options to manage user profiles that might pose an
increased security risk to your O365 tenant:
- View a list of existing external users with access to your tenant
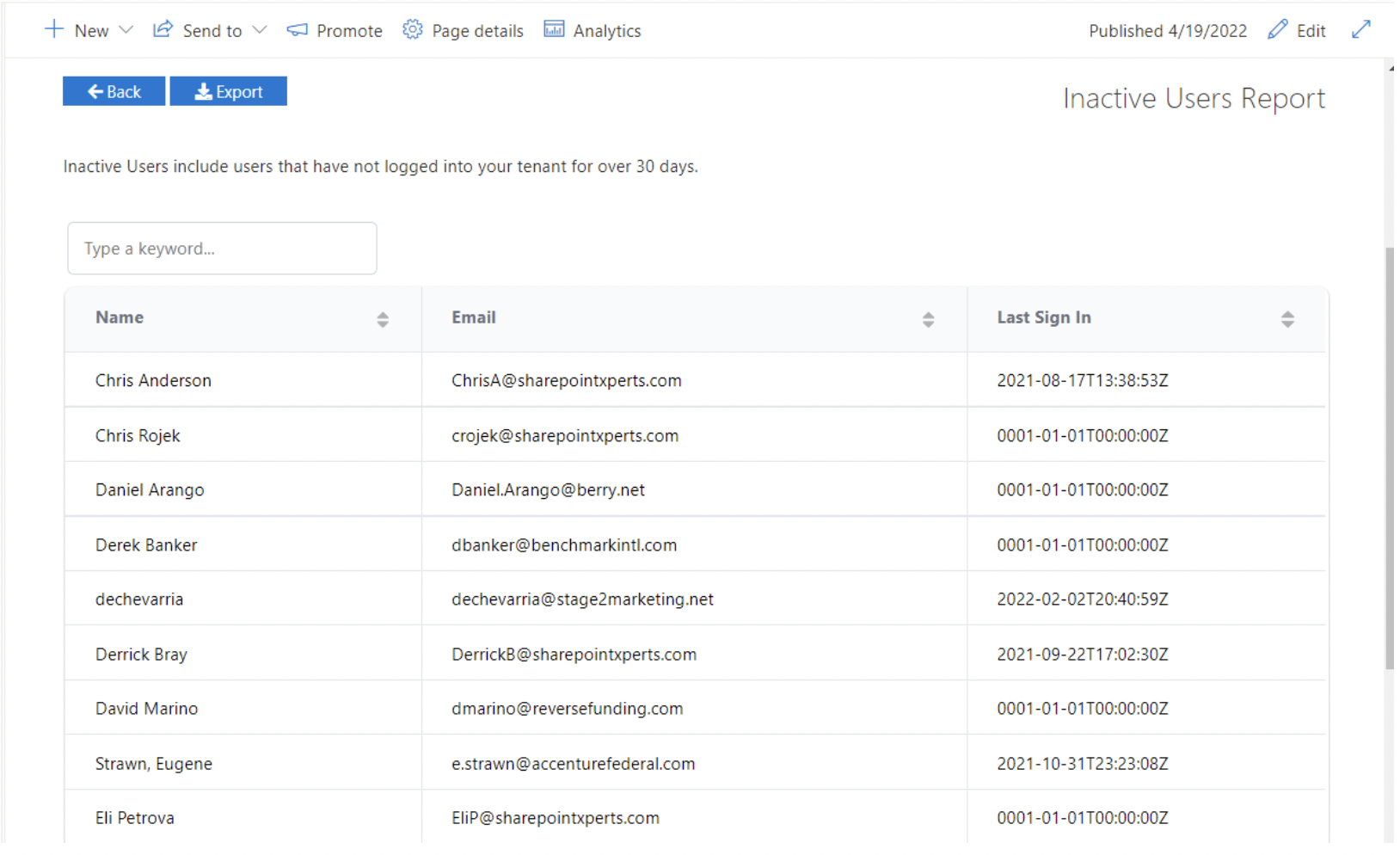
- View a list of inactive users who still have access to your tenant
- View a list of users who have access to your tenant, but no active licenses
- The ability to keyword search inside any of the above lists
- Export functionality for all lists generated from Security Audit Plus
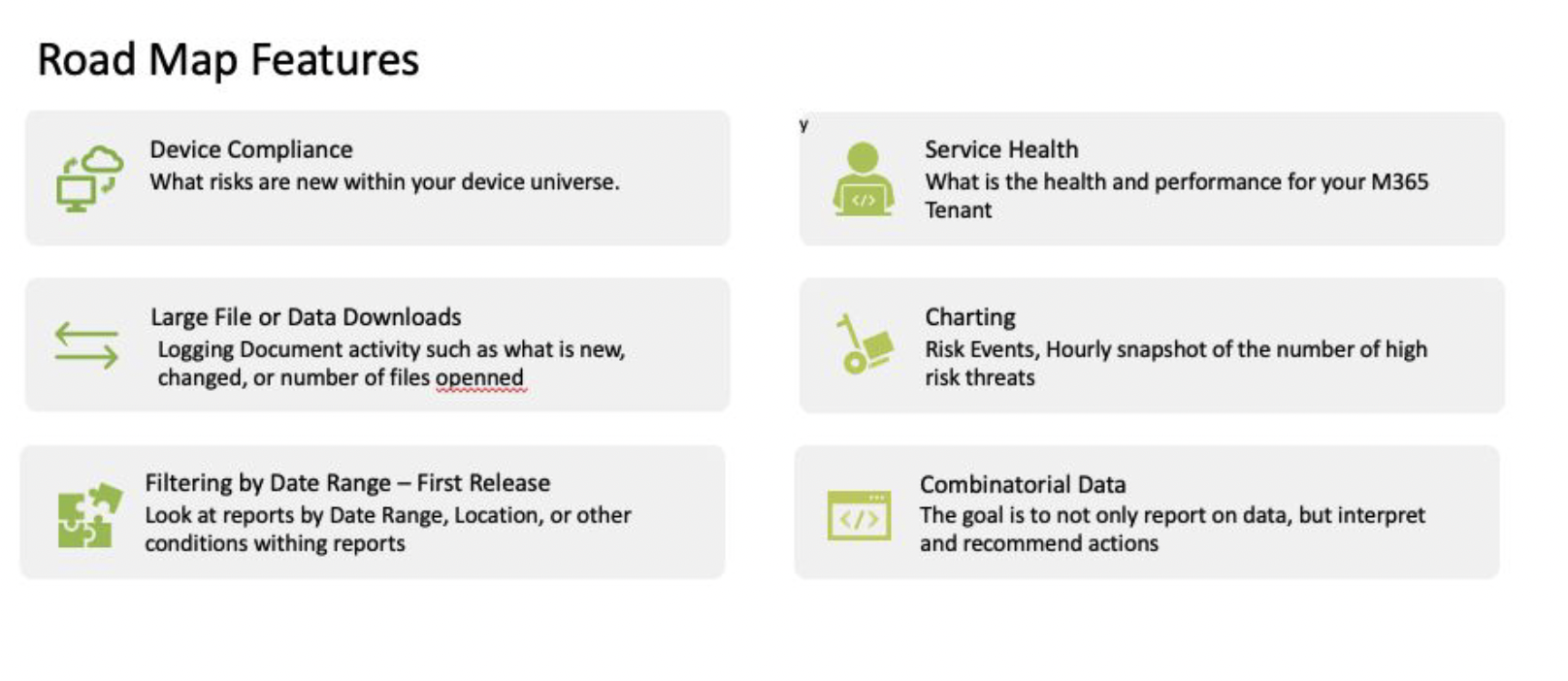
Risk Events & Security Metrics
Additional audit features offered by Security Audit Plus include:
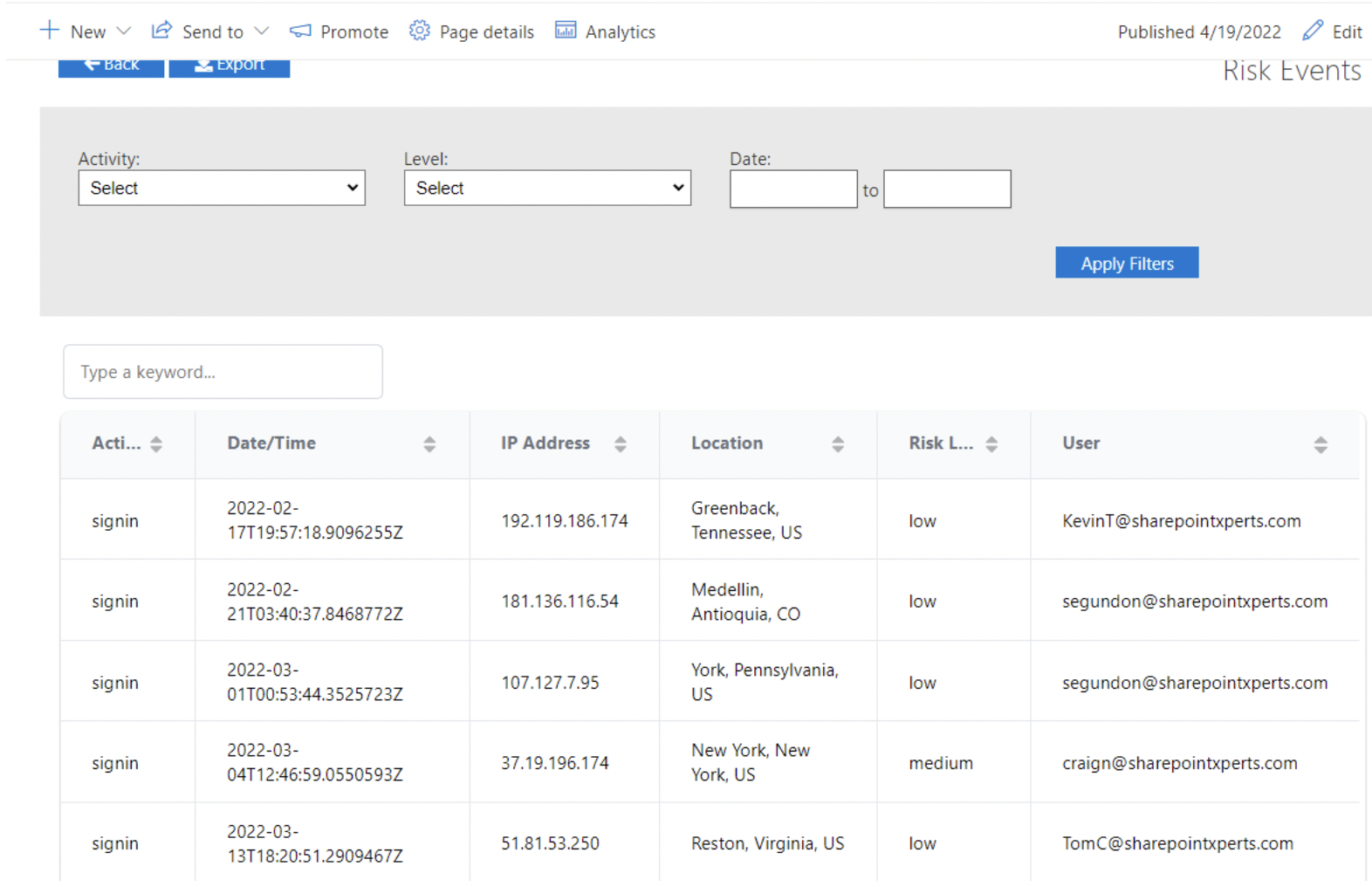
- Review a list of high-risk events that have occurred in your O365 tenant using the “Risk Events” tile
- Obtain security metrics for your tenant using the “Security Metrics” tile
- Review corrective actions that can be taken after viewing the security metrics
- Features are locked down to very specific permission groups to prevent security breaches
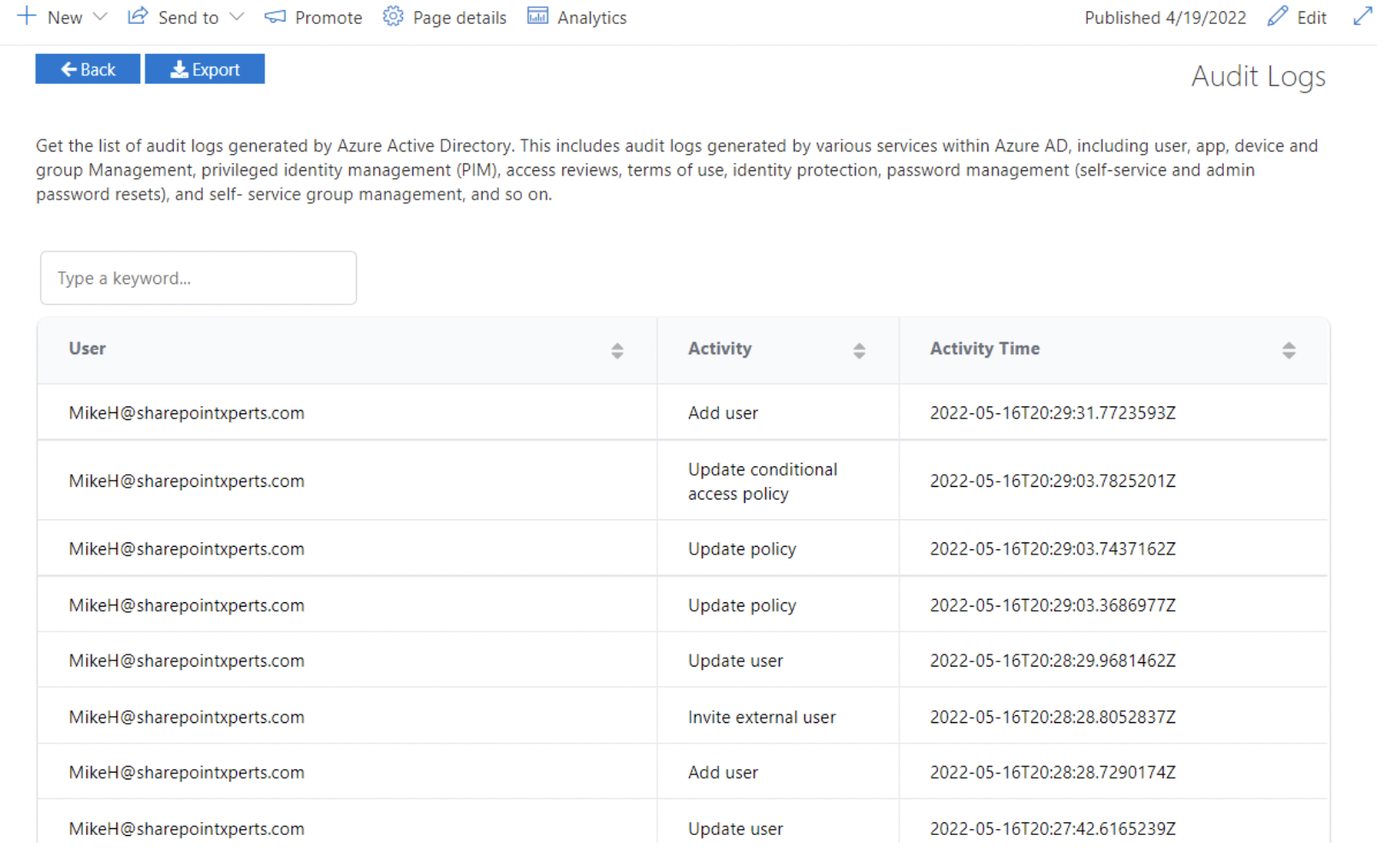
Azure AD Audit Logs
Get a list of all audit logs generated by Azure Active Directory.
- Permissions are locked down to only very specific groups only to prevent security breaches
- Results can be sorted and exported
- Keyword search is also available
An Ounce of Prevention is Worth a Pound of Cure
Bamboo’s Security Audit Plus provides you with ways to prevent cyber attacks within your organization with security risk prevention and management for your M365/SharePoint environment in one easy-to-navigate tool.
You have access to a centralized cybersecurity dashboard that gives you a bird’s-eye view of the most dangerous cybersecurity events that could affect you, with an ever-growing suite of features that keep you safe.